Sharing key business information with strategic partners, vendors, and third-party service providers has never been more critical than it is today—nor has it come at such a high cost. Operational risks are skyrocketing as new data sources crop up across the business, leaving even the best-resourced organizations struggling to close critical gaps in third-party data risk management. In this article, we dive into the growing complexities of third-party data sharing, outlining best practices and tools that organizations can use to keep their business protected in an age of accelerated information sharing.
The third-party data trap: Friend today, foe tomorrow
Think about all of your company’s data: customer information, financial records, and internal reports. What if it's incomplete, inaccurate, or exposed to wrong folks inside the organization? That's data risk. Now, think about the business details you share or receive from partners, suppliers, or outside companies. Third-party data risk is when an external party mishandles the information you’ve shared with them or the data they give you is inaccurate, incomplete, outdated, impermissible for use, or subject to other risk factors. Third-party data risk can show up in many different ways—from simple inventory mistakes to newsworthy security breaches—and it’s a problem for every stakeholder involved. Poor third-party data management practices can lead to a host of business problems such as:
- Greater security risks. Not only do business leaders need to worry about data leaving the company, but data coming in requires strict oversight as well. A lot of business leaders treat incoming data as inherently reliable when in reality they don’t know where it came from or how securely it was handled before reaching them. This lack of provenance (i.e., data history) can expose the company to major security risks.
- Increased compliance costs. Complying with evolving data regulations is expensive, and the costs are only going up. Third-party data sharing amplifies these challenges, making it even harder to audit business data to ensure it meets compliance standards. This creates significant gaps when it comes to managing evolving regulatory environments effectively.
- Unforeseen operational disruption. Keeping operations running smoothly requires real-time data, whether it comes from partners, loyalty programs, or cloud services. Poor-quality data can disrupt everything from on-time deliveries to customer service. In other words: managing third-party data risks isn’t only about security—it’s about ensuring your company has trusted, reliable information to run at its best 24/7.
- Negative customer experiences. Imagine booking a flight using a mobile airline app. Today’s consumers expect to do everything in one place: pick a seat, earn loyalty points, manage billing, maybe even add a rental car or hotel stay. This often involves several partner companies and tons of data flying around behind the scenes. If the data being shared isn't reliable and up-to-date, customers get frustrated, support teams become overwhelmed, and costs skyrocket.
- Complicated settlements and billing. When it comes to exchanging financial data with other companies, the information needs to be accurate and reliable. If there’s any doubt about its accuracy or security, things only grow more expensive. Companies might hold onto extra cash reserves, create complex systems to fix mistakes, or hire more people to reconcile and validate their data.
Common third-party data management roadblocks
Unfortunately, traditional data infrastructure and governance tools can’t keep pace with the complexities of modern data sharing. Think about your company's data like it’s sitting in a giant warehouse. In the past, all this data belonged solely to the company, neatly organized on shelves. This made managing data fairly simple: categorize it, store it securely, and control access. The problem? That's not how business data works anymore. Today, data is everywhere: in the cloud, with business partners, and constantly moving through a web of connections (APIs, cloud storage, email, etc.). That giant warehouse of data? It now sits on top of a complex highway system with data speeding in and out from every direction. Even finding data you truly "own" is often a challenge. A lack of visibility and control over continuously flowing data streams now creates serious problems for business leaders:
- Who's to blame? If something goes wrong with the data or it’s used in an improper way, it's difficult to pinpoint who's responsible and why.
- Trust issues: Can businesses trust the data they're using? Is it accurate, complete, and up-to-date? How can they be 100% certain?
- Legal headaches: Companies are increasingly responsible for data they don't even control, making legal and regulatory compliance a recurring nightmare.
The trouble with conventional data catalogs and governance tools is that they’re designed for the “closed warehouse” model—not the evolving dynamics of multi-party data sharing. They were built to manage internal data, not the information flowing between multiple companies.
This brings about challenges such as:
- Data silos & blind spots: Important data might be hidden in unknown or inaccessible locations, making it hard for the right people to find and use.
- Data canyons: Information gaps exist when data travels between companies, systems, and geographies—creating confusion and risk.
- Unreliable data: Data arrives without a clear history or origin, making it inherently untrustworthy.
- Data exhaust mishaps: Sharing data without critical business context (i.e., metadata) can lead to compliance issues across parties.
These data challenges are a growing risk for businesses of all sizes. However, by understanding why these challenges exist, and implementing a comprehensive third-party data risk management approach, companies can expertly navigate this complex landscape to reduce risk.
From chaos to control: Tools for lowering third-party risks
While third-party risk management is a firmly established corporate governance activity, even well-resourced companies are struggling to scale existing data governance processes across their partner network. Here, consider incorporating the following best practices and tools into your third-party risk management program:
- Automatic data-usage enforcement: First, establish clear data-usage agreements with all third parties and partners, outlining appropriate data-handling practices, data residency requirements, and data breach notification procedures. Then, automate these processes with smart contracts, which immediately flag and enforce third-party infractions the moment they occur.
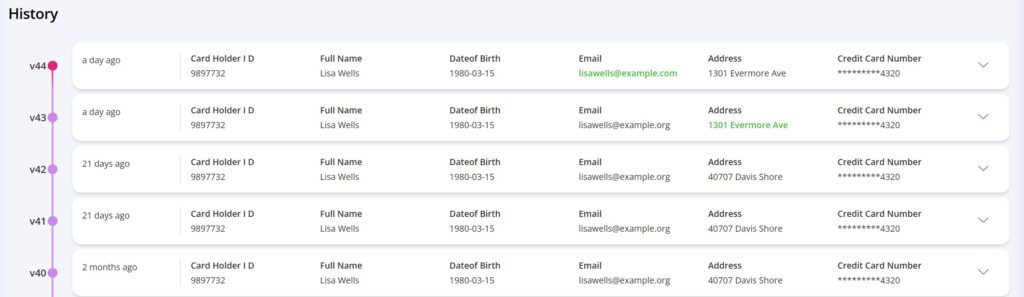
- Proactive auditing and governance: Third-party data risks require different oversight than traditional auditing methods, which are slow and manual. This is where visibility into data access changes, lineage, and read receipts inside your data risk management solution become extremely valuable. For example, read receipts can tell you who viewed a specific data item, what tools they used to access it, and when. Visibility into data access changes and lineage also lets you see what parties had access to a specific data item at a defined point in time.
- Routinely measure third-party risk scores: Implement a comprehensive risk scoring system to regularly evaluate the severity and likelihood of various risks across all of your third-party integrations and data exchange mechanisms.
- Standardize partner onboarding policies: Implementing automated data-sharing policies during partner onboarding is a quick, cost-effective way to bring new partners onto your network while keeping tight control over their access to your shared data.
- Implement modern data automation tools: Finally, leverage advanced technology such as modern data automation platforms to automate complex multi-party data movement, streamline external audits, and extend data governance across your partner network.
By implementing these robust processes and tools, your organization can gain complete oversight and control over third-party data exchange to better mitigate risks and safeguard the business from potential harm.


